Facile and Equipment-Free Data Encryption and Decryption by Self-Encrypting Pt(II) Complex | ACS Applied Materials & Interfaces
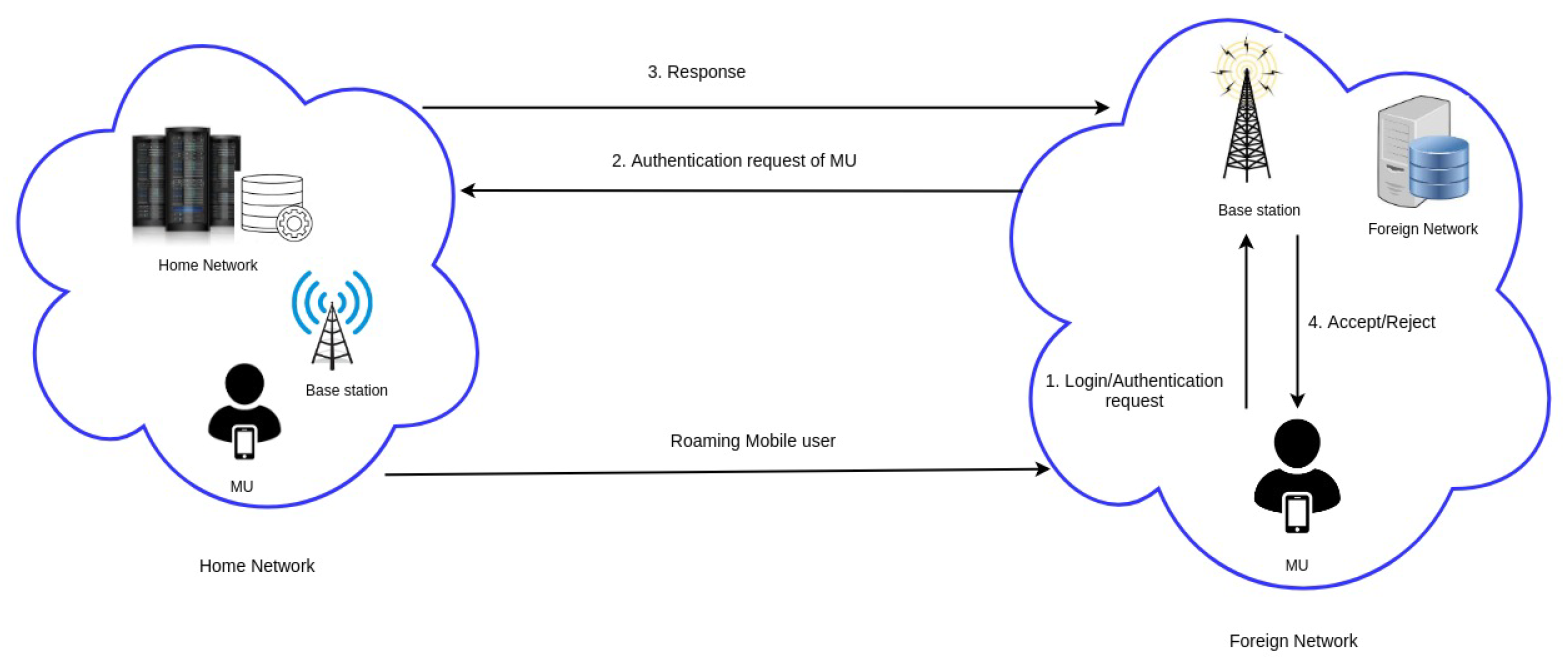
Cryptography | Free Full-Text | ES-HAS: ECC-Based Secure Handover Authentication Scheme for Roaming Mobile User in Global Mobility Networks

COMPUTER SITX 3000 - Mobile Self Encryption Project.doc - Mobile Self Encryption Project This project allows users to store sensitive data on their mobile phones | Course Hero